Science and Technology
8 Key Steps to Launching Your Taxi App Clone
Learn the 8 key steps to launching your taxi app clone and enter the lucrative world of ride-hailing..
Science and Technology
automated penetration testing
automated penetration testing, in which security professionals perform deliberate attacks on systems..

Science and Technology
World Wide Web with Windstream Internet - Coverage & Availability
Windstream Internet offers high-speed internet connectivity to customers across the United States, d..

Science and Technology
Achieving DevOps Harmony: Sirius360's Guide to Your Current State Analysis
Sirius360 pioneers DevSecOps advancement, offering expert consultation and implementation. Evaluate ..

Science and Technology
Ecommerce Seo Services - Wiselok Tech Solution
Welcome to Wiselok Tech Solution, your ultimate destination for cutting-edge digital marketing, web ..

Science and Technology
Streamlining Cloud Infrastructure Setup: Proven Methods for Efficiency and Reliability
Establishing a robust cloud infrastructure requires configuring servers, storage, networking, and vi..
Science and Technology
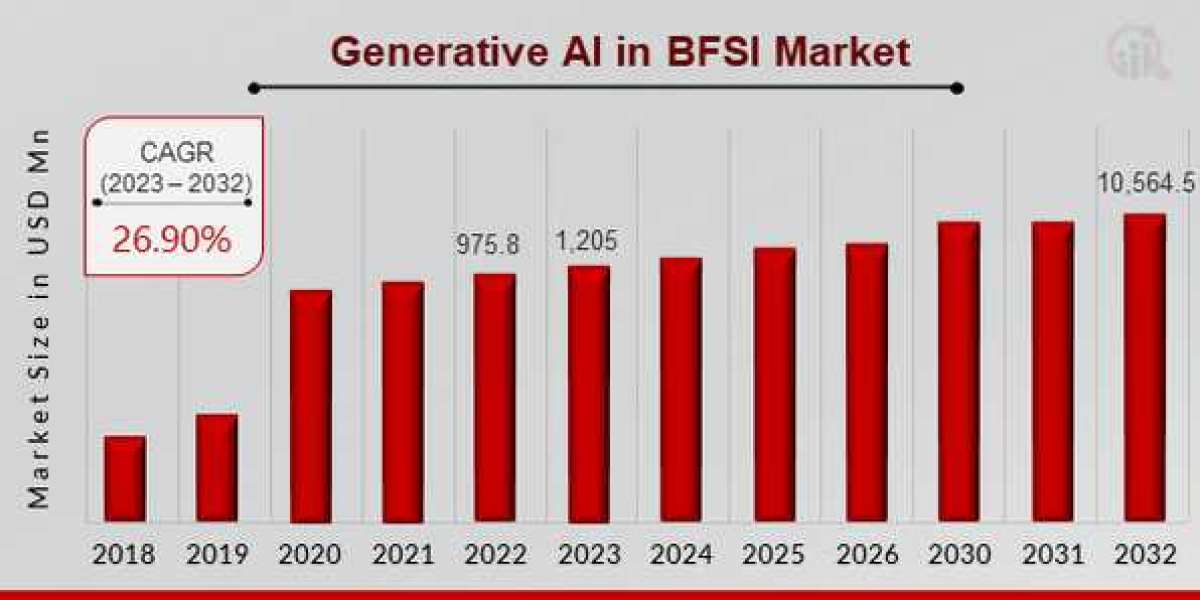
US Generative AI in BFSI Market Regional Analysis 2032
According to the search results, the Generative AI in BFSI Market size is projected to grow from USD..

Science and Technology
Empowering Healthcare through Custom Software Solutions
Experience innovation in healthcare technology with Shubpy Solutions Pvt Ltd...
Science and Technology
The Rise of White-Label Delivery Apps: Changing the Dynamics of Business
Discover how white-label delivery apps transform the business landscape in this insightful explorati..

Science and Technology
Shielding Your Assets: A Guide to Effective Cyber Security Consulting Services
Cyber Security Consulting provides tailored strategies and solutions to assess, mitigate, and manage..





